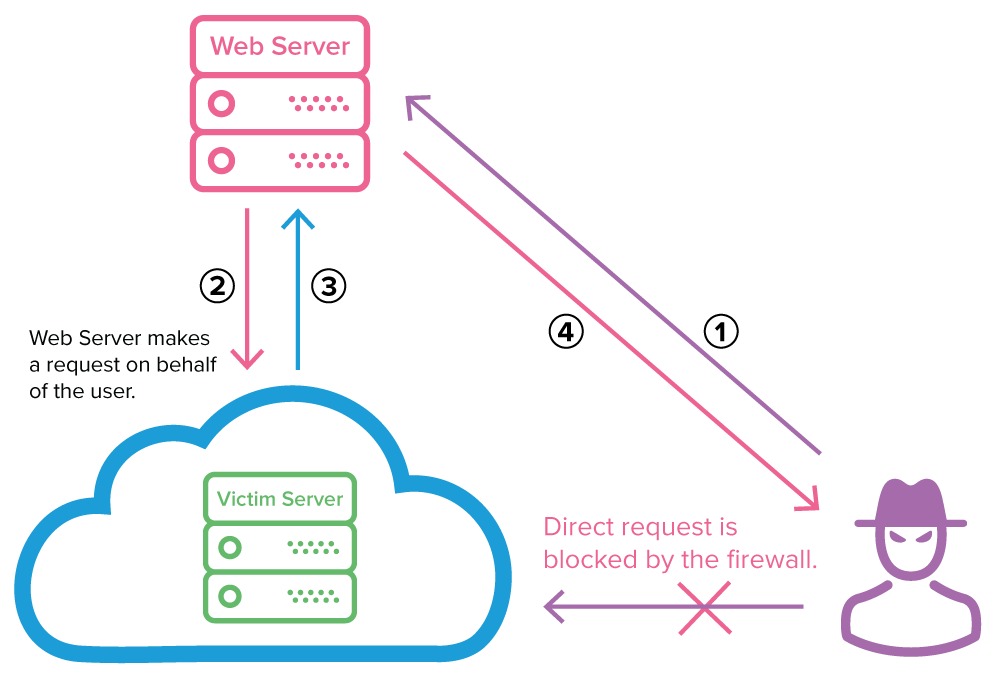
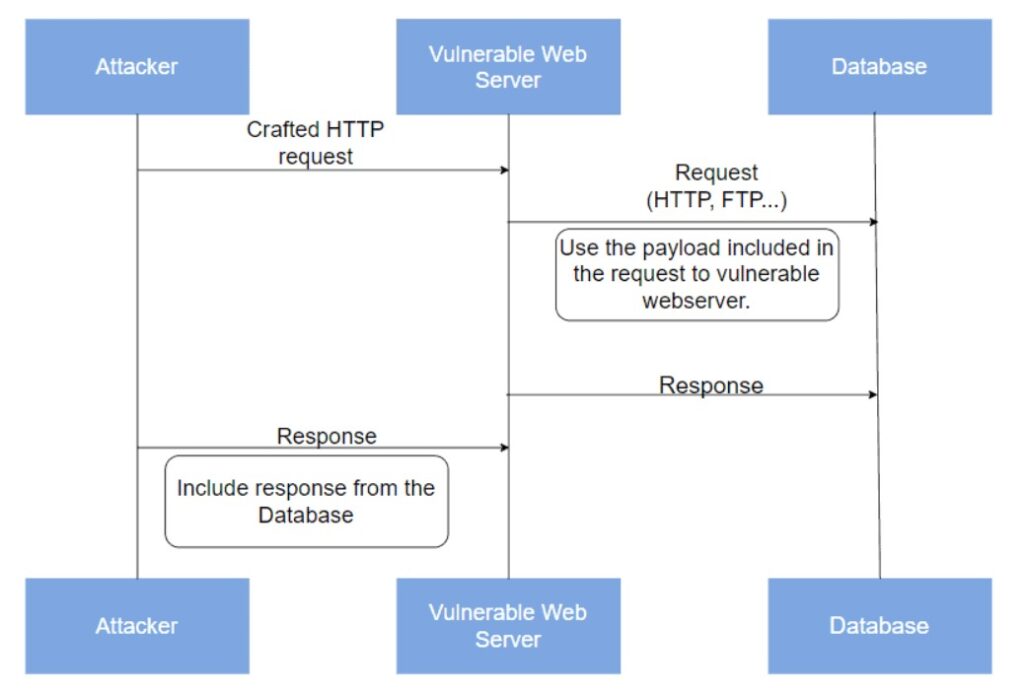
Server-Side Request Forgery (SSRF) is a critical web security vulnerability that allows attackers to manipulate a server into making unintended HTTP requests to arbitrary destinations. In cloud environments, SSRF attacks pose particularly severe risks as they can lead to unauthorized access to sensitive instance metadata, temporary IAM credentials, and internal cloud resources.
The Instance Metadata Service (IMDS) is a fundamental component of cloud infrastructure that provides EC2 instances with access to metadata and temporary security credentials. With the evolution from IMDSv1 to IMDSv2, AWS has significantly enhanced security measures to combat SSRF-based attacks.
Understanding SSRF vulnerabilities in the context of cloud security is crucial for developers and system administrators, as recent campaigns have shown attackers actively exploiting these vulnerabilities to steal cloud credentials and gain unauthorized access to AWS resources.
Section 1: What is SSRF?
The Concept of SSRF
Server-Side Request Forgery occurs when an application accepts user input and uses it to make HTTP requests without proper validation. This allows attackers to:
• Manipulate server behavior: Force the server to make requests to unintended destinations
• Bypass network security controls: Access internal services not directly accessible from the internet
• Extract sensitive information: Retrieve data from internal APIs and metadata services
How SSRF Vulnerabilities Are Exploited
Attackers typically exploit SSRF through several attack vectors:
1. URL Parameter Manipulation: Modifying URL parameters to point to internal services
2. File Upload Exploits: Using file upload functionality to trigger server-side requests
3. Webhook Abuse: Manipulating webhook URLs to access internal resources
4. API Endpoint Exploitation: Leveraging API endpoints that fetch external resources
Real-World Examples and Consequences
Recent security research has documented several concerning trends:
• Targeted EC2 Campaigns: Since mid-2024, threat actors have been systematically exploiting SSRF vulnerabilities in websites hosted on AWS EC2 instances
• Credential Theft: Attackers successfully extract temporary IAM credentials through IMDS access
• Lateral Movement: Stolen credentials enable unauthorized access to additional AWS resources and services
• Data Exfiltration: Compromised instances serve as pivot points for broader cloud infrastructure attacks
Section 2: The Role of IMDS in Cloud Security
Instance Metadata Service Overview
The Instance Metadata Service (IMDS) serves several critical functions:
• Credential Management: Provides temporary, automatically-rotating IAM credentials
• Instance Information: Supplies metadata about the EC2 instance configuration
• Security Token Service: Eliminates the need to hardcode sensitive credentials
• Application Integration: Enables secure application authentication with AWS services
IMDSv1 vs. IMDSv2: Key Differences
| Feature | IMDSv1 | IMDSv2 |
| Authentication | Simple HTTP GET requests | Token-based session authentication |
| Request Method | Direct metadata access | Two-step process with PUT token request |
| SSRF Protection | Vulnerable to SSRF attacks | Resistant to SSRF exploitation |
| HTTP Methods | Supports GET requests | Requires PUT for token, then GET for data |
| Hop Limit | No built-in protection | Configurable hop limit for request forwarding |
Security Improvements in IMDSv2
IMDSv2 introduces several critical security enhancements:
1. Session Authentication: Each request requires a secret token obtained via HTTP PUT
2. Request Signing: Tokens must be included in subsequent metadata requests
3. Time-Based Tokens: Session tokens have configurable TTL (Time To Live)
4. Request Method Enforcement: Eliminates simple GET-based access patterns
Section 3: SSRF Risks Associated with IMDSv1
Specific Risks of IMDSv1
IMDSv1 presents several vulnerabilities that attackers actively exploit:
• Direct HTTP Access: Simple GET requests to http://169.254.169.254/latest/meta-data/
• No Authentication Required: Metadata accessible without additional security measures
• Credential Exposure: IAM temporary credentials easily retrievable
• Network Traversal: Vulnerable to request forwarding through proxies and load balancers
SSRF Exploitation Scenarios
Attackers can exploit SSRF vulnerabilities in IMDSv1 environments through:
# Example SSRF payload targeting IMDSv1
http://vulnerable-app.com/fetch?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/
Potential Data Exposure and Unauthorized Access
Successful SSRF attacks against IMDSv1 can result in:
• IAM Role Credentials: Access to temporary AWS API keys
• Instance Metadata: System configuration and network information
• User Data: Bootstrap scripts and configuration data
• Security Group Information: Network access rules and restrictions
Section 4: Mitigation Strategies for SSRF with IMDSv2
Implementing IMDSv2 Security Controls
Core IMDSv2 Implementation Steps:
1. Token Acquisition:
TOKEN=$(curl -X PUT “http://169.254.169.254/latest/api/token” -H “X-aws-ec2-metadata-token-ttl-seconds: 21600”)
2. Authenticated Metadata Access:
curl -H “X-aws-ec2-metadata-token: $TOKEN” http://169.254.169.254/latest/meta-data/
Comprehensive Mitigation Strategies
Access Control Implementation
• Enforce IMDSv2 Only: Disable IMDSv1 across all EC2 instances
• Configure Hop Limits: Set appropriate hop limits to prevent request forwarding
• Network Segmentation: Implement VPC security groups to restrict metadata access
Input Validation and Sanitization
• URL Validation: Implement strict whitelists for allowed destinations
• Protocol Restrictions: Block internal IP ranges and metadata endpoints
• Request Method Controls: Validate and restrict HTTP methods used in requests
Network-Level Protections
• Security Groups: Configure restrictive outbound rules
• NACLs (Network Access Control Lists): Implement subnet-level traffic filtering
• WAF Rules: Deploy Web Application Firewall rules to detect SSRF attempts
Application-Level Security
• Least Privilege IAM: Assign minimal necessary permissions to instance roles
• Service Role Segregation: Use distinct roles for different application components
• Credential Rotation: Implement automated credential rotation policies
Section 5: Best Practices for Securing Cloud Environments Against SSRF
Developer and System Administrator Guidelines
System Hardening
• Regular Updates: Maintain current security patches across all systems
• Configuration Management: Use Infrastructure as Code for consistent security settings
• Monitoring and Alerting: Implement comprehensive logging for metadata access attempts
Security Testing and Validation
• Penetration Testing: Conduct regular SSRF vulnerability assessments
• Code Reviews: Implement secure coding practices in development workflows
• Automated Security Scanning: Use tools to detect potential SSRF vulnerabilities
Monitoring and Detection
• Application Firewalls: Deploy WAFs configured to detect SSRF patterns
• Intrusion Detection: Monitor for unusual metadata service access patterns
• Log Analysis: Implement centralized logging for security event correlation
Security Training and Awareness
• Developer Education: Provide training on secure coding practices
• SSRF Awareness: Educate teams about common SSRF attack vectors
• Incident Response: Develop procedures for handling suspected SSRF attacks
Implementation Checklist
• Enforce IMDSv2: Disable IMDSv1 across all EC2 instances
• Configure Hop Limits: Set appropriate metadata service hop limits
• Implement Input Validation: Validate all user-supplied URLs and parameters
• Deploy Network Controls: Configure security groups and NACLs
• Enable Monitoring: Implement logging for metadata service access
• Conduct Security Testing: Regular penetration testing and vulnerability assessments
• Train Development Teams: Provide SSRF awareness and secure coding training
Conclusion
SSRF vulnerabilities represent a critical threat to cloud environments, particularly when combined with IMDSv1’s inherent security weaknesses. The evolution to IMDSv2 provides robust defenses against SSRF attacks through token-based authentication and enhanced request validation.
Organizations must adopt a comprehensive security approach that includes:
• Immediate IMDSv2 Implementation: Transitioning away from vulnerable IMDSv1
• Layered Security Controls: Combining network, application, and access-level protections
• Continuous Monitoring: Implementing detection capabilities for SSRF attempts
• Security Training: Ensuring development teams understand SSRF risks and mitigation strategies
The threat landscape continues to evolve, with attackers actively targeting SSRF vulnerabilities in cloud environments. Adopting a proactive security posture and implementing IMDSv2 controls is essential for protecting cloud infrastructure and sensitive credentials.
Call to Action
Stay Secure and Informed:
• Subscribe to AWS Security Bulletins for the latest threat intelligence
• Join cloud security communities for best practice sharing
• Implement regular security assessments and updates
Additional Resources:
• OWASP SSRF Prevention Cheat Sheet
Keywords: SSRF, Server-Side Request Forgery, IMDSv2, AWS security, cloud security, metadata service security, EC2 security, vulnerability mitigation, instance metadata service, IAM credentials, SSRF prevention, cloud infrastructure security
References:
1. AWS Documentation – Instance Metadata Service Configuration
2. Hacking The Cloud – SSRF to EC2 Metadata Exploitation Techniques
3. Resecurity Research – SSRF to AWS Metadata Exposure Analysis
4. Datadog Security Labs – IMDSv2 Enforcement Guidelines
5. AWS Security Blog – IMDSv2 Implementation Benefits
